Why Are Strings Immutable in Java? Comprehensive Guide for Beginners
Wiki Article
The Evolution of Immutable String Handling: A Vital Aspect of Software Growth
In the detailed realm of software application growth, the handling of unalterable strings stands as a keystone that has undertaken significant development with time. From its simple origins to the complicated tests experienced in early executions, the trip of unalterable string adjustment has been a vital facet of software program design. As we navigate with the historical landscape of this basic idea, mapping the improvements, safety and security effects, and emerging fads, we locate ourselves at a juncture where the inherent worth of recognizing this development becomes progressively obvious.Beginnings of Immutable Strings
The principle of unalterable strings traces back to the early days of programming languages when programmers sought to improve the dependability and safety and security of information taking care of systems. Unalterable strings refer to strings that can not be transformed after they are created. This basic principle was introduced to resolve issues relating to information stability and protect against unintentional alterations to critical info kept as strings.
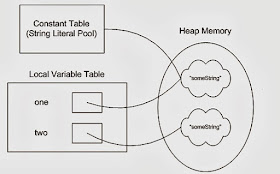
Furthermore, unalterable strings add to boosting the general safety and security of software application systems (Why are strings immutable in Java?). By stopping unauthorized celebrations from damaging delicate string data, unalterable strings help reduce the danger of data breaches and unauthorized access to secret information. This foundational idea remains to play a crucial duty in contemporary shows languages and stays a keystone of protected and durable software program advancement techniques
Very Early Challenges and Solutions
One of the primary obstacles in handling immutable strings was taking care of memory efficiently. In addition, making certain that strings stayed unaltered verified to be complex, particularly when multiple components of the codebase needed to gain access to and customize data.To resolve these difficulties, designers began implementing data security techniques to protect delicate info stored in immutable strings. Encryption helped safeguard data from unapproved accessibility and adjustment. Additionally, the introduction of hashing formulas gave a method to verify the stability of unalterable strings by creating one-of-a-kind checksums based on their materials. If any alterations had taken place, these checksums allowed for fast comparisons to identify. By including file encryption and hashing techniques into the handling of immutable strings, programmers significantly enhanced the safety and security and dependability of information within software systems.

Innovations in String Immutability
In software application growth, a significant advancement in the handling of unalterable strings has arised through developments in information file encryption and hashing techniques. By using safe hash algorithms like SHA-256 or cryptographic techniques such as AES file encryption, designers can make sure that delicate details saved in immutable strings continues to be safe and tamper-proof. These advancements have boosted the honesty and discretion of data within applications, especially in sectors where information security is paramount, such as cybersecurity, finance, and medical care.Moreover, advancements in string immutability have led the way for improved performance optimization. Unalterable strings allow for more efficient memory monitoring and caching approaches, lowering the expenses connected with regular string adjustments (Why are strings immutable in Java?). This optimization not just improves the total responsiveness of software applications yet likewise adds to much better scalability and resource usage
Safety Ramifications and Ideal Practices
With the structure laid by advancements in string immutability, recognizing the safety and security effects and implementing ideal methods becomes paramount in securing delicate data within software application applications. Immutable strings play a crucial function in boosting safety by protecting against unauthorized alterations to information, ensuring information honesty throughout the application's lifecycle. By making use of unalterable strings, developers can minimize typical vulnerabilities such as injection assaults, barrier overflows, and data meddling, which are frequently exploited by malicious actors to jeopardize systems.This consists of encrypting information at rest and in transit, carrying out correct gain access to controls, using protected coding methods, and frequently upgrading software parts to patch known susceptabilities. By integrating these safety and security procedures and ideal practices into software application advancement processes, companies can better shield their information assets and minimize the risk of security breaches and data leakages.
Future Fads in String Handling
In the middle of the ever-evolving landscape of software application development, the trajectory of string handling is positioned to witness considerable innovations and technologies. One of the vital future fads in string handling is the enhancing concentrate on efficiency optimization. As software application applications continue to expand in complexity and range, the efficient handling of strings ends you could try here up being vital for keeping ideal performance. Programmers are exploring new algorithms and data frameworks to improve the speed and effectiveness of string operations.In addition, another pattern coming up is the combination of expert system (AI) and artificial intelligence (ML) in string managing jobs. AI-powered devices are being created to automate and streamline different string control procedures, bring about increased productivity and accuracy in software program growth operations.
Moreover, there is an expanding emphasis on boosting the safety and security facets of string managing with advanced encryption strategies and secure coding methods. As cyber dangers remain to advance, ensuring the integrity and discretion of data within strings is ending up being a leading priority for programmers. By adopting durable protection steps, such as encryption at rest and in transportation, More Bonuses programmers can mitigate the threats connected with string adjustment vulnerabilities.
Final Thought
In final thought, the advancement of unalterable string handling has been a crucial facet of software program development, beginning with its origins to the innovations made in recent years. Early difficulties have been dealt with with ingenious solutions, causing enhanced safety and security techniques in handling strings. It is very important for programmers to stay updated on the most up to date patterns in string immutability to make sure the toughness and safety of their software program applications.Unalterable strings refer to strings that can not be changed after they are developed. Why are strings immutable in Java?. By avoiding unauthorized parties from meddling with delicate string data, unalterable strings help alleviate the danger of information breaches and unapproved access to private info. By incorporating encryption and hashing approaches right into the handling of unalterable strings, designers significantly boosted the protection and dependability of information within software application systems
Immutable strings permit for more effective memory administration and caching strategies, minimizing the expenses linked with see post constant string controls. Immutable strings play a critical function in boosting safety and security by preventing unapproved modifications to information, making certain data integrity throughout the application's lifecycle.
Report this wiki page